Using Postman to access Azure Active Directory protected Azure Functions
You can enable Azure Active Directory authentication on Azure Functions in the Azure portal without having to write any code. Navigate to Function app, Platform features, then Authentication/Authorization:
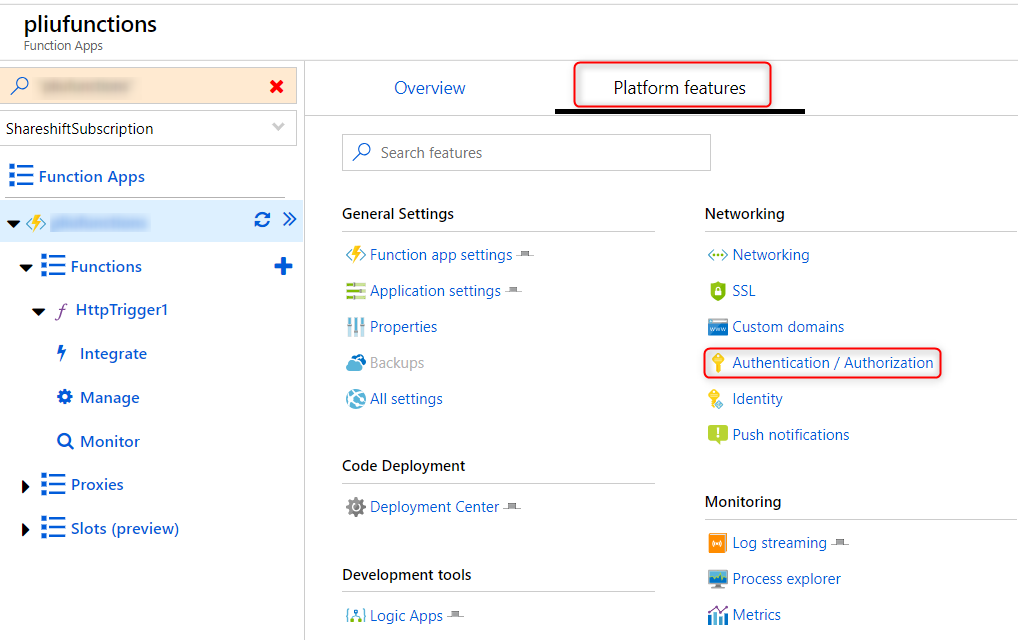
You can then configure different authentication providers. Here we choose Azure Active Directory (AD). Follow the UI wizard to complete the configuration. client_id below refers to the client id of the application you registered in Azure AD for this Function app.
Assuming your Function uses HTTP trigger, you can access the Function from Postman in two ways.
Use a browser to get access code
- In the browser, issue a request
https://login.microsoftonline.com/common/oauth2/authorize?client_id=<client_id>&response_type=code&redirect_uri=http://localhost. Make sure http://localhost is one of the registered reply URLs. - The browser will redirect back with a “code” parameter in the URL. Copy the value of this parameter.
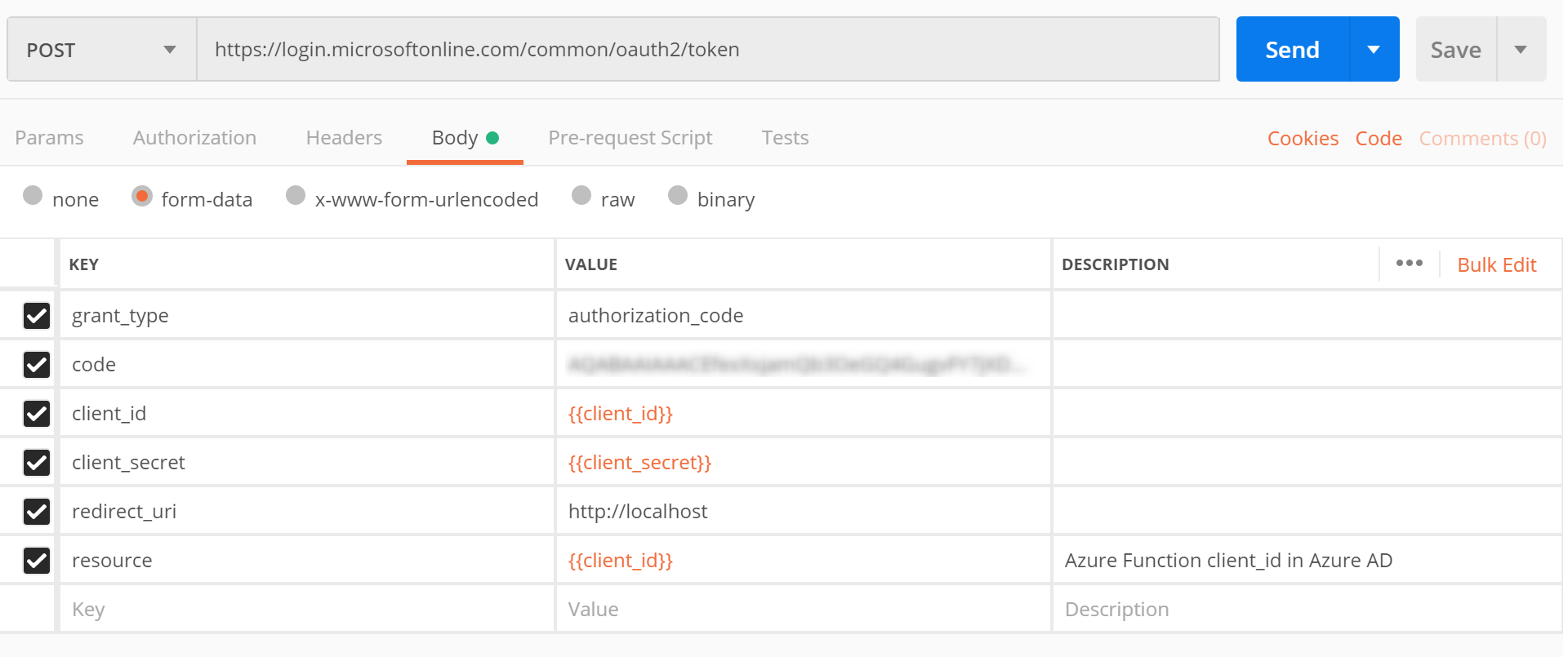
- In Postman, make a POST request. The value of the “code” parameter is the value you copied from the previous step. Copy the “access_token” from the response.
- In Postman, make a POST request with the “access_token”:
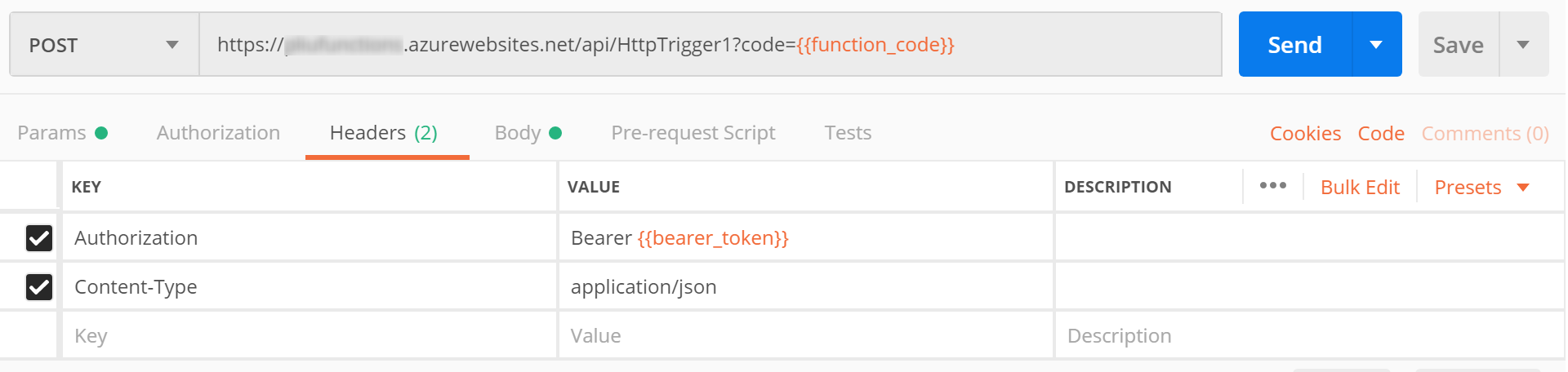 You can get the URL of your function from the Azure portal.
You can get the URL of your function from the Azure portal.
Use Postman OAuth2
With Postman OAuth2, you can authenticate within Postman entirely without a browser. I verified that multi-factor authentication also works with username/password plus mobile authentication, but using a smartcard doesn’t work at the time of writing (Jan 2019).
-
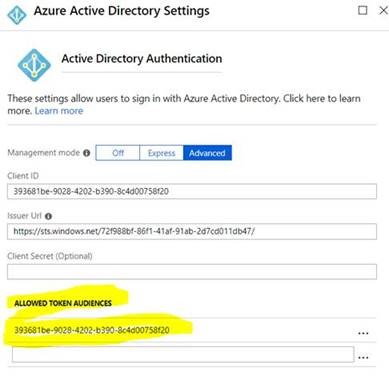
Go to your Function App in Azure portal, Authentication / Authorization, Azure Active Directory, turn on Advanced option, and add the client_id of the Function app to ALLOWED TOKEN AUDIENCES:
-
Compose a call to Azure Function in Postman, then choose Authorization tab, and OAuth 2.0 to get an access token:
- Fill in the values in the OAuth2 screen, make sure:
- Callback URL must be registered in your Azure AD app as one of the reply URLs
- Auth URL must include a “resource” parameter which can be the same as the client_id of Function app, for example,
https://login.microsoftonline.com/common/oauth2/authorize?resource=client_id - Scope and State can be empty
- Client Authentication should be set to Send client credentials in body. This is the mode supported by AAD.
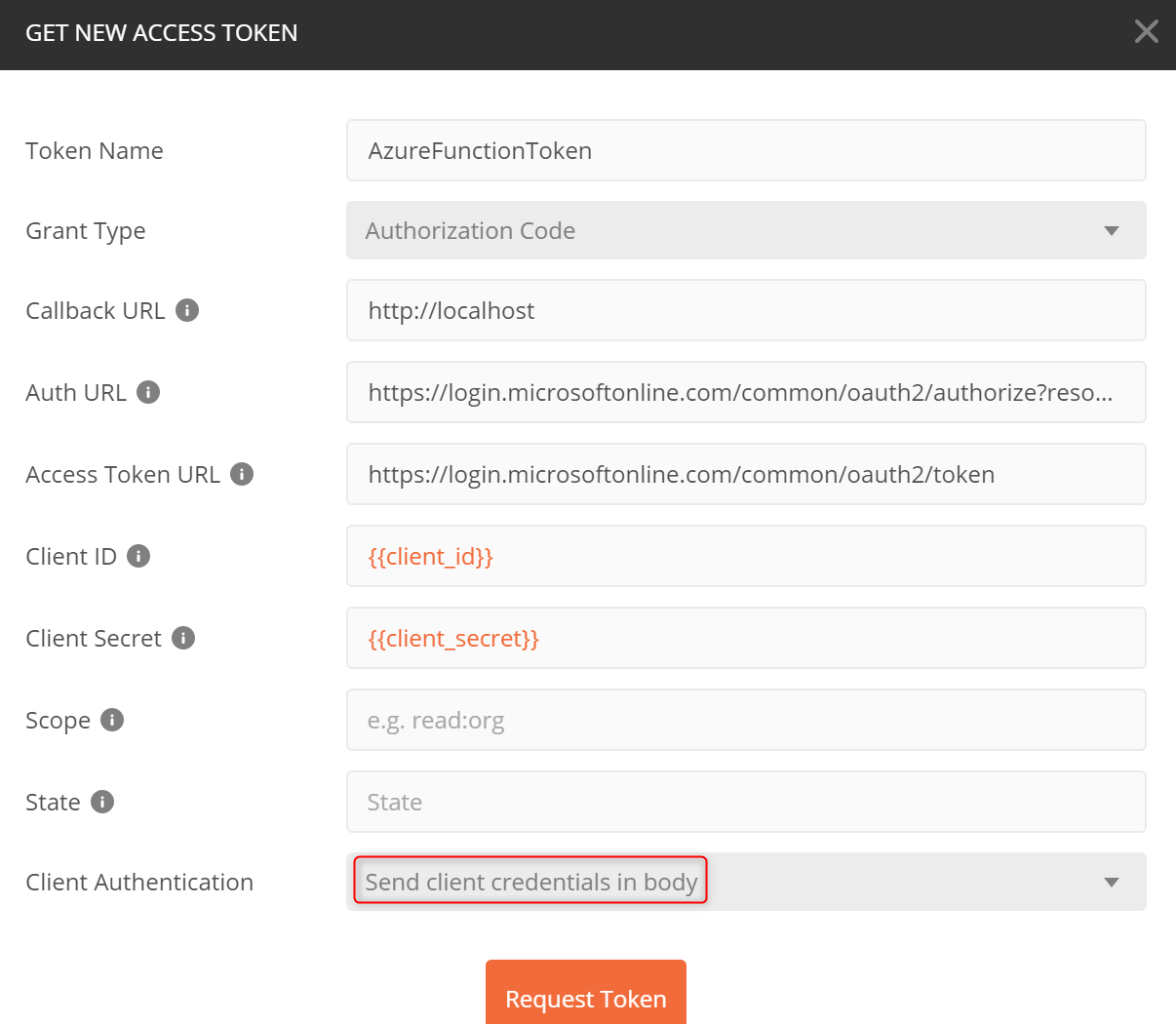
- Use the obtained token to make the call.